Blockchain & Bitcoin: Hashcash or SHA-256

If you are following the post series, you’ve learned that hashcash is the proof-of-work algorithm used by bitcoin mining. Let’s get technical and explore more about hashcash in this post.
A hash function is an algorithm that takes data of any length as an input and produces a bit string of fixed length, named the hash value. The hash value is always the same for the same input data.
Bitcoin uses SHA256^2 as its proof-of-work function. SHA256^2 is the application of the SHA256 hashing function twice. SHA256 is part of a set (SHA-2) of hash functions designed by the NSA and published by NIST in 2001.
The SHA (Secure Hash Algorithm) is a cryptographic hash function. A cryptographic hash is like a signature for a text or a data file. SHA-256 algorithm generates an almost-unique, fixed-size 256-bit (32-byte) hash. SHA-256 is one of the successor hash functions to SHA-1, and is one of the strongest hash functions available. Hash is a one-way function – it cannot be decrypted back. This makes it suitable for password validation, challenge hash authentication, anti-tamper, digital signatures.
SHA256 has two additional properties: One-wayness, and Strong collision resistance.
One-wayness: Given the hash value, it must be computationally infeasible to find out the input data. This is a key property for the application of proof-of-work.


Computationally infeasible means that there is no known algorithm that can recover the message within a time that is related to the size of the input. What this means in practice is that the extreme amount of time to break a hashing function makes it very impractical to do so.
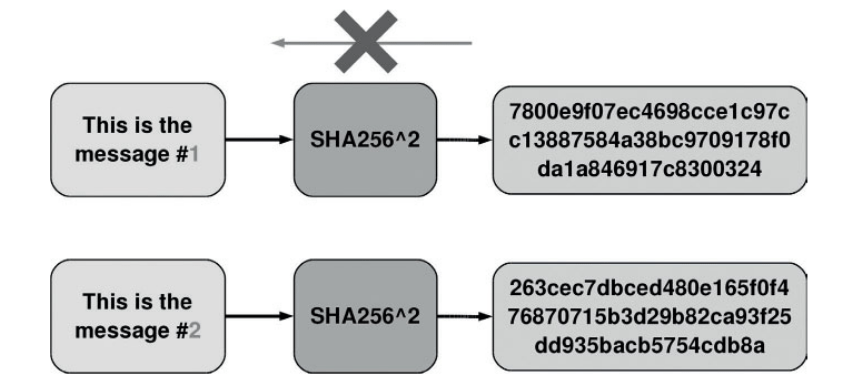
Strong collision resistance. It means that it is computationally infeasible to find two input data points that result in the same hash value.
As for the current cryptography hashing algorithm, the NIST has published SHA-3 in 2015. It might be used in the future if there is known collisions or its computationally capable to break the SHA-2. You should now have a brief idea on how SHA-2 is used for proof-of-work in mining process.
Enjoy Learning!



